In the contemporary digital ecosystem, where every aspect of life—from banking and communication to healthcare and professional work—is conducted online, the integrity of our personal and financial data hinges entirely on one thing: strong passwords. Unfortunately, the average user juggles dozens, if not hundreds, of online accounts, leading to the use of weak, reused, or easily guessable passwords. This habit is the single greatest vulnerability exploited by cybercriminals. The solution to this modern dilemma is the Password Manager, an indispensable software tool that transforms chaotic, insecure login habits into a seamless, robust, and automatic defense system.
For publishers leveraging Google AdSense and aiming for superior SEO performance, the topic of “Password Manager Tools” is immensely valuable. It targets an audience with high commercial intent, attracts premium cybersecurity advertisers, and falls under the critical “Your Money or Your Life” (YMYL) category, demanding exhaustive, expert-level content. This comprehensive, 2000-word article will delve into the functionality, benefits, security architecture, and vital role of password managers in establishing a modern, impenetrable digital security posture.
The Digital Password Crisis: Why We Need Managers
The need for password managers stems from a fundamental conflict between human psychology and digital security requirements. Security experts demand long, complex, unique passwords for every site, but the human brain struggles to memorize more than a handful of random strings.
The Fatal Flaws in Human Password Habits
A. Reusing Passwords: Studies consistently show that most users reuse the same password (or slight variations) across multiple, often dozens, of websites. A single data breach on a low-security site can compromise the user’s high-security accounts (like email or banking) through a simple technique called credential stuffing.
B. Weak and Guessable Passwords: Users often choose dictionary words, simple number sequences (e.g., “123456”), or personal information (names, birthdates) that are easily cracked by automated brute-force attacks or dictionary attacks.
C. Note-Taking Insecurity: People resort to insecure methods like writing passwords on sticky notes, saving them in unencrypted text files on their desktop, or using unsafe cloud documents, which are easily accessible to anyone with physical or remote access to the device.
D. Password Fatigue: The mental exhaustion resulting from continually creating, entering, and changing complex, unique passwords leads to poor security choices out of sheer frustration.
The Fundamental Requirement: Entropy
High-security passwords must possess high entropy—a measure of their randomness and unpredictability. A robust password should be long (12+ characters), contain a mix of uppercase and lowercase letters, numbers, and symbols, and have no connection to the user’s personal life or common phrases. Only a password manager can reliably generate, store, and recall hundreds of such high-entropy strings without user effort.
Core Functionality of a Password Manager
A password manager is essentially an encrypted digital vault that stores all your login credentials, personal information, and secure notes. It operates under a single, user-created Master Password—the only password the user ever needs to memorize.
The Three Pillars of Protection
A. Secure Password Generation: The manager features a built-in generator capable of creating mathematically random, high-entropy passwords of customizable length and character complexity. It eliminates the “human bias” in password creation.
B. Encrypted Storage: All stored data is secured using military-grade, industry-standard end-to-end encryption, typically AES-256. The data is encrypted locally on the user’s device before it is synchronized to the cloud (if applicable). Crucially, the Master Password is the only key to decrypting this vault.
C. Automatic Filling and Login: Through browser extensions and mobile apps, the manager automatically detects the correct username and password for a site and fills the login fields with a single click or tap. This eliminates typing errors and protects against keylogging (software that records keystrokes), as the information is programmatically injected.
Advanced Features for Comprehensive Security
D. Secure Sharing: Allows users to securely share specific login credentials or documents with trusted individuals (e.g., family members or colleagues) without revealing the actual password in plain text.
E. Two-Factor Authentication (2FA) Integration: Many modern managers include a built-in Time-based One-Time Password (TOTP) generator, consolidating the storage of both passwords and 2FA codes into one highly secured vault, simplifying the login process while maintaining high security.
F. Password Health Monitoring: The software actively scans the stored vault for weak, reused, or aged passwords. It also checks credentials against public databases of known data breaches, alerting the user immediately if their passwords have been compromised (a feature often called Dark Web Monitoring).
Security Architecture: How Encryption Provides Trust
The fundamental question users ask is: “If one master password protects everything, isn’t that a single point of failure?” The answer lies in the robust, non-negotiable security architecture used by reputable password managers.
Zero-Knowledge Architecture (ZKA)
The gold standard for password managers is the Zero-Knowledge Architecture (ZKA). This design principle ensures absolute user privacy and security.
A. Local Encryption: Encryption and decryption always occur locally on the user’s device. The Master Password never leaves the device and is never transmitted over the internet.
B. No Master Key on Servers: The password manager company itself never knows or stores the user’s Master Password, nor does it possess the encryption keys necessary to decrypt the user’s vault data.
C. Impossibility of Decryption: In the event of a successful cyberattack against the password manager company’s cloud servers, the stolen data is nothing more than meaningless, encrypted binary code. Without the user’s Master Password (which is not stored on the server), the data is impossible to decrypt, rendering the breach harmless to the user.
Encryption Protocol: AES-256
The vast majority of reputable password managers utilize the Advanced Encryption Standard (AES) with a 256-bit key length.
D. Strength of AES-256: AES-256 is the standard adopted by the U.S. government and militaries for protecting classified information. It is considered computationally unbreakable by current technology. The time required for even the most powerful supercomputers to crack an AES-256 key through brute force is effectively longer than the estimated age of the universe.
E. Key Derivation Functions (KDF): To further secure the Master Password and prevent brute-force attacks against the offline vault copy, a slow, resource-intensive Key Derivation Function (KDF) like PBKDF2 (Password-Based Key Derivation Function 2) or Argon2 is used. This process intentionally slows down the process of trying potential Master Passwords, making brute-force attacks economically and physically infeasible.

Enhancing Security Beyond Passwords
A truly effective security strategy leverages a password manager for much more than just login credentials.
Secure Note and Document Storage
A. Encrypted Information: The vault is ideal for storing sensitive, non-login information that should never be in plain text. Examples include copies of software license keys, passport numbers, tax identification numbers, Wi-Fi passwords, and insurance policy details.
B. Sharing Credentials Securely: Instead of emailing or texting a family member a new garage code or bank PIN (which leaves a permanent, unencrypted copy on servers and devices), secure notes can be shared and revoked within the manager’s encrypted environment.
Leveraging Multi-Factor Authentication (MFA)
C. The TOTP Advantage: By integrating the TOTP function, the password manager becomes a single source of truth for both factors of authentication. The user can auto-fill the password and then automatically generate and fill the time-based code, reducing the reliance on a separate physical device (like a phone) and significantly speeding up the login process without sacrificing the security MFA provides.
D. Security vs. Convenience Trade-off: The manager successfully shifts the traditional security vs. convenience trade-off. It provides the highest levels of security (unique, complex passwords plus 2FA) while simultaneously offering maximum convenience (one master password and auto-fill).
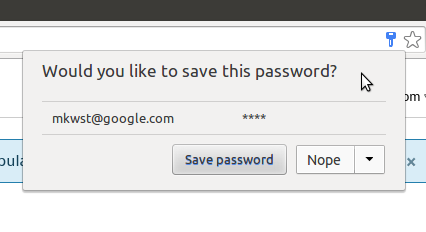
The Indispensable Role of Password Managers in SEO & AdSense
For content creation, the topic of password managers is a gateway to high-profit monetization and superior SEO performance within the lucrative cybersecurity vertical.
A. High Commercial Intent and CPC
Users searching for “best password manager,” “password manager reviews,” or “password manager comparison” have clear commercial intent—they are ready to purchase or subscribe to a service.
-
This intent drives a high Cost-Per-Click (CPC) from competing password manager companies (e.g., LastPass, 1Password, Bitwarden) placing ads via Google AdSense. Long, authoritative content maximizes the page view time and ad impressions.
B. E-A-T and YMYL Authority
As a YMYL (Your Money or Your Life) topic, Google rigorously evaluates the Expertise, Authority, and Trust (E-A-T) of the content. A 2000-word analysis that details:
-
The difference between AES-256 and other encryption standards.
-
The function of KDFs like PBKDF2/Argon2.
-
The critical concept of Zero-Knowledge Architecture.
This comprehensive technical depth establishes the content as a leading authority, which is essential for ranking highly in competitive, high-stakes security searches.
C. Low Bounce Rate and High Dwell Time
Structured, easy-to-read, and detailed technical content keeps the reader engaged. A user searching for complex security information will stay on a page that clearly explains Zero-Knowledge and AES-256, leading to a low bounce rate and high dwell time. These engagement metrics are powerful signals to Google that the content is valuable, boosting search rankings and, consequently, traffic and AdSense revenue.
Practical Steps to Implementing a Password Manager
Transitioning to a password manager is a critical security upgrade that requires a structured approach.
A. Choosing the Right Manager: Evaluate options based on their security audits, Zero-Knowledge commitment, supported platforms (Windows, macOS, iOS, Android), and cost (free or premium). Focus on managers that publicly document their security architecture.
B. Creating an Unbreakable Master Password: This is the single most important step. The Master Password must be long (ideally 15-20 characters), highly complex, and unique. It should be memorized and never written down or stored digitally.
C. Importing Existing Data: Most managers offer tools to import existing passwords from browsers or other files, centralizing the data quickly.
D. The Cleanup Phase (The Great Reset): Once imported, use the manager’s health audit feature to identify all reused and weak passwords. Systematically visit each site and use the manager’s generator to create a new, unique, complex password, immediately strengthening the overall security posture.
E. Enabling Multi-Factor Authentication (MFA): Set up MFA (using a separate app like Google Authenticator or the manager’s built-in TOTP function) on the password manager account itself. This adds a critical layer of defense to the primary vault.
Conclusion
In a world defined by persistent cyber threats and overwhelming digital complexity, the password manager is no longer a luxury—it is a mandatory security tool. It resolves the intrinsic human conflict between convenience and security, providing a practical, scalable, and mathematically sound defense against the vast majority of online security threats.
By adopting a manager and committing to its foundational principle—one complex, memorable Master Password protecting hundreds of unique, complex, computer-generated passwords—users move from a state of constant vulnerability to a position of security by default. This digital fortress ensures that even if one account is compromised through a phishing scam, the rest of the digital life remains securely locked away, providing the peace of mind necessary to thrive in the modern digital age.